Consider this: As of 2020, 123456 remains the most common password according to Nordpass. And if you asked, “Who would use such a weak password?” we’d answer that 2,543,285 people worldwide do. Take into account other research that states that an average person has around 70-80 passwords.
A password is only one of the standard security methods, a unique combination of characters you create and use as a key to authenticate yourself. The same concept stands behind a token, except that it’s generated by a computer. Both methods are widespread to protect and access data in banking applications, personal profiles, or corporate networks. And both have similar drawbacks, i.e., they can be forgotten, stolen, or hacked.
With advances in biometric technologies, a new concept – what-you-are authentication – emerged, presenting a more secure and convenient way to validate a person’s identity. In this article, we’ll explore what biometrics are, which data is used for different types of biometric systems, and how to adopt one.
What are biometrics?
Biometrics are measurements of a human body’s unique physical or behavioral parameters. These measurements, stored in a form of encrypted code, are used as a personal identifier. The most common type of biometrics to verify identity is a fingerprint any modern smartphone can scan.
Biometrics create a secure and reliable way to access a system or application as the data on your one-of-a-kind physical traits can’t be lost, replicated, or guessed. Which makes it fairly difficult to steal a user’s identity. And if that isn’t enough, you don’t have to memorize dozens of passwords or store tokens.This protects the target system from fraud on both ends.
Depending on their functions, all biometric systems can be divided into two categories — authentication and identification. Let’s look at each operation case in detail and define where they can be used.
Biometric system operations
Biometric systems generally compare the existing samples of biometrics with the provided one, to tell if there is a match or not. They, however, apply different logic and computation mechanics to verify a person. So, there are two main operations: authentication and identification.
Authentication
Authentication (or positive identification) is the process of validating your identity with “one-to-one” comparison. Once a person claims to be “User X,” the system knows which data is to be compared. Say, it checks a newly provided fingerprint against the previously scanned one.
Identification
Identification (or negative identification) has an opposite flow. In this case, we want to make sure that a certain identity doesn’t match the one stored in the database.
Such technologies are widely used in criminalistics, government institutions, surveillance, and healthcare. The system enrolls provided data to compare it with all the available samples, so this is a “one-to-many” comparison. The accuracy of a comparison is traditionally measured in the percentage of false positive or false negative results. Usually, negative identification is more resource intensive, as each enrollment requires more computing power.
For instance, Canada’s Border Services Agency collects fingerprints and digital photographs of visa applicants. Their biometric identification system checks the collected samples against the database of criminals or migrant overstayers.
Despite differences, both types of systems utilize similar architectural components. Now, let’s analyze which software and hardware parts constitute these technologies.
Biometric system components
In its simplest representation, a biometric system has only five components:
- a data input sensor that performs data intake,
- a data interpreter,
- a data storage,
- a processing unit, and
- a user interface.
Here, we’ll also describe additions that can be present in biometric technologies. Besides that, we’ll elaborate on the general flow of the process for each component.
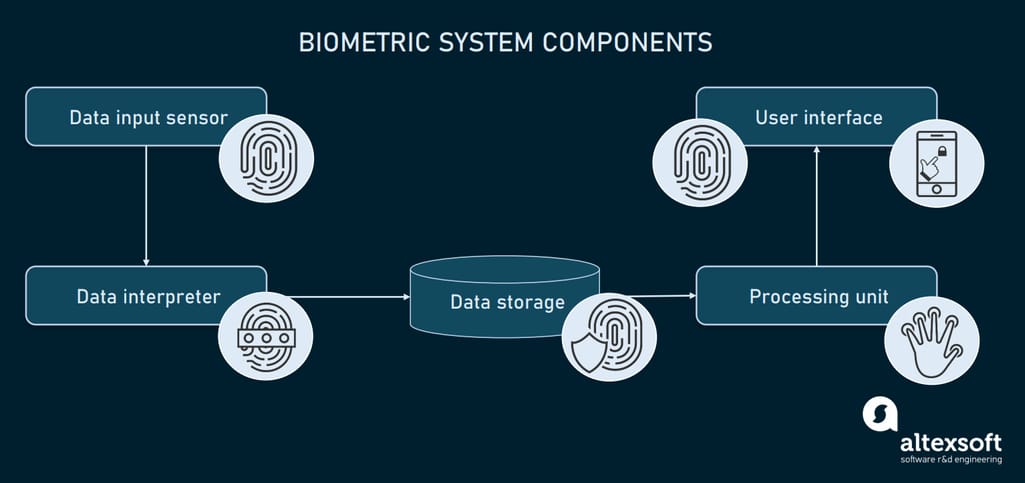
Biometric system components
Data input hardware sensor
The first component is a sensor device that collects biometric data. The type of sensor will depend on which biometric data we want to collect. Some of the most common are
- fingerprint scanners,
- iris/retina sensors,
- cameras for face and gait recognition,
- microphones for voice recognition,
- computer keyboards for keystroke dynamics analysis, and
- infrared scanners for vein pattern recognition.
The sensor may perform different tasks, depending on the biometric system and the data it gathers. In the case of authentication, it will rescan an object in question to compare it with a prior sample. If a system is trying to identify the user, it may scan multiple objects constantly, checking if there is no match with the target objects in the database.
Data interpreter
Contrary to a popular belief, biometric data is never stored as a set of common images. No matter what type of biometrics, the captured sample is interpreted into a numeric string by a dedicated software program called a data interpreter.
Say, in the case of facial recognition, an interpreter may generate a numerical ratio that describes the distance between the eyes, shape and radius of a chin, size of a nose, etc. Fingerprints or eye scans are also converted in digital formats. However, not all the biometrics can be processed this way, owing to the complex structure of a specific measurement. For example, vein patterns are stored as an encrypted image.
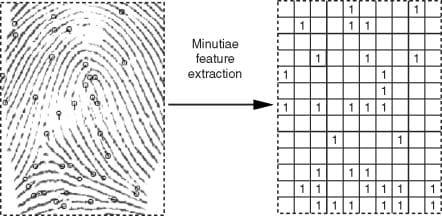
An example of the minutiae feature extraction from a fingerprint sample
Source: sciencedirect.com
Additionally, an interpreter performs the encryption of the retrieved data into an unreadable format to protect it from duplication, counterfeiting, or any other fraud actions. This makes the information more secure from identity theft, even if it is stolen from the database.
Biometric data storage
After transformation, the data is moved to a storage. There are several options for storing data.
- On-device storage. In case your smartphone or laptop acts as an input module, the scanned data is stored on your personal device and can’t be reached by the biometric provider. This is because the store for biometrics is located on a dedicated chip that’s not a part of the device memory card, but still can be accessed only from your device.
- Biometric server. For corporate systems, a more common case is a cloud-based repository that communicates with a sensor device.
- Distributed storage. It utilizes both server memory and on-device storages.
The data samples stored in a database will be triggered each time a user enrolls the comparison.
Biometric processor
A biometric processor is a software element that performs calculations to find similarities between biometric data. As we’re speaking about the numeric values, processors are mostly presented by an algorithm that compares values between each other.
As a result, it provides a similarity score that has to reach a certain threshold to be indicated as a match (or no match). Depending on the aim of the comparison and the type of biometric data, the threshold will have a certain level of tolerance.
User interface
Typically, biometric systems have a graphic user interface to give instructions on how to use the scanner, which data is required, etc. The user interface also displays the comparison results.
A separate dashboard is accessible for biometric system administrators to modify the system, resolve comparison issues, and manage the platform as a whole.
In some cases, biometric systems include different types of sensors to take in multiple types of biometric data or two types of sensors to read both physical and digital information. For example, some government institutions take your fingerprint data from a scanner and biometrics from your passport chip.

A biometric authentication tablet
Source: cardlogix.com
Now, let’s look at what biometric data can be taken for identification purposes and what technologies exist for each specific data type.
Biometric data types and use cases
Not every piece of our physiological parameters can be used for identification purposes, because some of them may vary greatly depending on stress level, temperature, mood, etc. Moreover, not all the measurements can provide a specific pattern. That’s why we use the parts of the human body that have a unique structure, like a human iris.

Biometric data types
All the biometric data types currently in use can be divided into two categories: physiological measurements and behavioral ones.
Physiological biometrics
Physiological parameters are the gold standard as they are easy to collect, unique, and provide the most accurate comparative features.
Fingerprint. They are the most common type of biometrics, due to the singular pattern of a human fingerprint, easy access, and multiple patterns that can be acquired from a single person. Fingerprint recognition is a dedicated technology that analyzes the structure of a sample. The everyday examples are various applications in social services, border control, social security, payment application, banking, insurance, and so on.
Vein (or vascular) pattern. Described far back in the 90s by the US FBI, vein patterns are often used instead of fingerprint scans. The advantage over the finger scanning is that it doesn’t require direct contact to provide the same level of accuracy, as vein patterns in fingers or palms also have a unique structure for individuals. The samples are taken using an infrared scanner that highlights vein structure under the skin.
As the application example, Yarco Company replaced its time tracking mechanism from cards to vein pattern scanners. The old system relied on the use of plastic cards to log working time. This required the payroll department to gather these logs across multiple office locations.
After installing vein pattern scanners and setting up a single database that records logs from all the locations, the company increased payroll processing efficiency by 90 percent. Additionally, the procedure of time logging became easier and faster for the employees.
Voice recognition. Probably, almost everyone is familiar with the voice assistant bots like Cortana, Okay Google, Siri, and Amazon Alexa. While bots come in many different flavors, all of them utilize a voice recognition technique, which is generally a biometric measurement.
In short, the human voice possesses certain characteristics as timbre, volume, pitch, and tone. All these measures can be interpreted into a waveform, where peak frequencies will denote the characteristics of a certain person’s voice.
Voice recognition is applied in mobile banking as an authentication method. Some of the known cases are HSBC, a multinational banking company, and BBVA. Both use voice authentication to allow customers to quickly log into the app.
Face shape. Due to the advances in computer vision technologies, it became possible for a computer to analyse the structure of a human face, using such devices as web cameras or photo cameras on our phones.
For instance, JetBlue airline applies facial recognition to allow a paperless boarding experience. IoT cameras installed on the gate recognize the passengers, retrieving their biometric data to validate the identity without checking the boarding pass and documents. Currently, over 500 flights were done with the help of this self-boarding gate.
Iris pattern. Iris pattern recognition is a noncontact method of scanning the complex texture of a person’s unique iris. According to the National Institute of Standard and Technology (NIST), the method provides from 90 to 99 percent accuracy.
The only drawback is that iris structure can change during over time and can be modified by certain diseases and iris disorders.
Retina pattern. The retina has a capillary pattern that remains mostly unchanged during a lifetime and produces more accurate results than the iris. For example, a Korean hospital implemented CMITech's ocular recognition system EF-45N. It utilizes iris/retina IDs to record patient entry into the surgery room, which is required by the country regulations. Since the technology provides touchless identification, this became a go-to solution for COVID-19 conditions.
Saliva. This fluid can potentially become the next standard in biometrics. Since the emergence of smart wearables that simplify saliva collection, it bears promise to become an identification method in healthcare and travel. Its chemical composition provides enough protein to indicate the user, while its structure isn’t as complex as blood.
Behavioral biometrics
The second category of biometric measurements relies upon the behavioral factors of an individual. These include
- mouse activity,
- keystroke dynamics,
- gait type,
- touchscreen behavior, and
- device movement (based on the gyroscope data.)
Behavioral biometrics tend to change because of stress factors and various circumstances such as fatigue, injuries, and so on. So, this type of measurement neither provides a high level of accuracy, nor offers a 100-percent unique pattern for each individual. However, there are some cases like the Bank of Utah that utilizes keystroke dynamics analysis as an authentication method for e-banking.
Biometric data regulations
While the use of certain biometrics depends on the application and purpose, such systems in general impose several adoption challenges on organizations. As we’re talking about the most private data, the government strictly controls its use and storage. So, the first challenge is studying all the data protection laws.
First of all, there is a whole range of general data privacy regulations you need to know about.
General Data Protection Regulation (GDPR) is a common data protection law that applies to all countries of the European Union, and businesses gathering data in these regions.
California Consumer Privacy Act (CCPA) is a set of regulations for California, describing specifics of data protection, and consumer rights.
California Privacy Rights Act (CPPA) is an extension of the previous regulation set that will be in force in 2023.
But, besides these laws, biometric data is subject to its own regulatory acts. Keep in mind that no existing act prohibits the collection of biometrics. Each of them imposes some obligations to businesses, and enlists certain standards. Let’s start with the US privacy laws.
Biometrics laws and regulations in the US
Biometric Information Privacy Act (BIPA) was enacted by the state of Illinois. The act contains a set of requirements and security standards covering the use of biometrics. In brief, the regulations cover such aspects as:
- the requirement to provide informed consent,
- limited disclosure of biometric data,
- data retention protection, and
- compliance with the industry standards concerning biometrics storage and transmission.
Similar regulatory laws exist in other states, so you might consider them also.
Texas law provides conditions nearly identical to BIPA, identifying the subject of regulation as “commercial purposes.”
Washington State House Bill (1493) bacame law in 2017, providing the terms and conditions of the use of biometrics both for businesses and individuals. The requirements to comply with Washington law are similar to those in Texas and Illinois. However, there is one important note: The Washington bill clearly states that the collection of biometric data is prohibited until informed consent is obtained.
New York State has also designed a set of regulations concerning data usage in biometrics. But as of 2021, these regulations are not in force.
Registry of USG Recommended Biometric Standards is a set of technological and organization standards provided by NIST. You can review the latest version 5.0 (dated by 2014). They describe the general terminology, data formatting standards, registry concepts, and other specifics of biometric data processing. All the businesses located in the US are recommended to comply with these regulations.
Biometric regulations in Europe
The current laws in the European Union countries don't have any unified, specific regulations for biometric data protection. GDPR and its forms (like UK GDPR) remain the major acts on data transmission, storage, and privacy protection for businesses. GDPR provides the definition of biometric data, which means the underlying regulations also cover fingerprint and face recognition technology use.
As of 2021, there are some draft legislations that impose regulations on the use of facial recognition technologies for social surveillance.
How to approach biometric adoption?
The availability of face and fingerprint recognition technologies via smartphones or laptops makes it relatively easy for any business to integrate biometric verification. Yet, you still have several things to consider before introducing this technology into your workflow. Below, we’ll run through basic recommendations on how to approach biometric system adoption.
Define the purpose of your biometric system
First, you need to understand what tasks you want to solve with biometrics: which system requires verified access, who its users are, and what type of data they can provide conveniently.
The answers will help you pin down the preferred authentication method: whether it’s face ID, fingerprint scanning, voice or iris recognition. As you might notice, biometric data differs by the degree of uniqueness and the complexity of collecting. So this can be a determining factor in your decision.
When identifying a person, things get pretty complex. Here, facial recognition is the most common method, because it doesn’t involve human interaction with the system. Computer vision algorithms recognize face shape patterns from live video feeds or photos. But utilizing such technologies always entails complying with regulations because personal data is involved.
Study the existing regulations in your region
As we’ve mentioned before, European countries and the United States treat biometric data differently. Moreover, the regulations vary from state to state within the US. But, generally, ignoring security measures and recommendations set in the local data protection laws can result in penalties and even court appearances.
So before searching for a biometric technology or provider, make sure you know all the local conditions and can comply with them.
Review your current ecosystem
There is no ultimate suggestion on how to prepare for biometrics. But what you should do is pay attention to your current ecosystem and security measures. The purpose of this check is to make sure that your database and system endpoints are protected from fraud and security breaches.
If you are a tech-savvy business with a huge ecosystem of distributed databases and various applications, the interconnectivity between them should also be checked to prevent data breaches.
Explore the market of biometric tools
The market of biometrics lists many vendors that offer solutions to businesses of all sizes. Some of the well-known multinational companies providing all sorts of biometric solutions are
The mentioned vendors position themselves as biometric-as-a-service, installing their software on desktop, mobile, and web-based platforms.
Check available APIs and SDKs
For a small project, integration with an API that provides access to required functionality can be the best fit. Via APIs, you’ll get tools for collecting and processing biometric data. Below are several available options.
Kairos Face Recognition API — a face detection and feature recognition API for photo and video content
Lambda Labs Face Recognition — face detection, feature recognition, and identification API, capable of identifying gender, age, and racial features by analyzing video content
Android Biometrics API — an open-source API for face or fingerprint authentication on Android devices
Apple Biometric Authentication — a developer guide for implementing Face ID and Touch ID, as well as Apple Pay authentication on iOS and Mac devices
DevelopFeng Gait Recognition API — a source code for implementing gait recognition via surveillance systems
Marian-Margeta API -- another gait recognition tool based on the implementation of a deep neural network
Microsoft Speaker Recognition API — a voice timbre tool for verifying and identifying the speaker
VoiceIt API — a hybrid API for multiple types of biometrics. It enables implementation of voice and face recognition for authentication purposes.
Other challenges of biometric adoption
The market of biometrics technologies is quite rich at the moment. Traditionally, vendors offer a full package of infrastructural elements and hardware to install at your organization. But the required set of technologies will substantially depend on the application. One of the most widespread are office security systems that use fingerprint scanners.
However, biometrics remain a quite controversial concept because of its intimate nature. On one hand, the way biometrics allow us to authenticate ourselves brings a lot of benefits. You don't create or memorize anything; your own body acts as your password. On the other hand, this approach presents a higher risk of identity theft in the case of security breaches, because the industry is still developing standards and measures on how to store these data, and how to use them.
So prior to choosing any technology or provider of a biometric system you should pay attention to the publicly available information. For example, in 2019, a Suprema based BioStar 2 biometric system experienced a security breach. This resulted in the exposure of 28 million biometric samples. The samples included fingerprint scans, face photos, encrypted passwords, and facial recognition data from a single database. That’s why the mistrust factor will remain in place until businesses learn how to protect biometric data from fraud.

